In this writeup I will show you how I solved the Bypass challenge from HackTheBox. The challenge is a very easy reversing challenge. Let’s start!
Initial Analysis #
Let’s start with downloading the challenge file from the HTB webpage and unzipping the archive.
> unzip Bypass.zip
[Bypass.zip] Bypass.exe password:
inflating: Bypass.exe
We have a single .exe file, now I run file on the exe file to see what kind of file it is.
> file Bypass.exe
Bypass.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
The file is a .Net assembly, googling around I found that .Net assemblies can be decompiled using dnSpy. Since our file is a x32 assembly, we need to use the x32 version of dnSpy.
DnSpy Analysis #
DnSpy is a tool that can be used to decompile .Net assemblies. It can be used to view the source code of the assembly, to edit the assembly and to debug the assembly. After opening the Bypass.exe file in dnSpy, we can see the source code disassebled. First of all I opened the class 0 which is the main class and contains the following code:
using System;
// Token: 0x02000002 RID: 2
public class 0
{
// Token: 0x06000002 RID: 2 RVA: 0x00002058 File Offset: 0x00000258
public static void 0()
{
bool flag = global::0.1();
bool flag2 = flag;
if (flag2)
{
global::0.2();
}
else
{
Console.WriteLine(5.0);
global::0.0();
}
}
// Token: 0x06000003 RID: 3 RVA: 0x00002090 File Offset: 0x00000290
public static bool 1()
{
Console.Write(5.1);
string text = Console.ReadLine();
Console.Write(5.2);
string text2 = Console.ReadLine();
return false;
}
// Token: 0x06000004 RID: 4 RVA: 0x000020C8 File Offset: 0x000002C8
public static void 2()
{
string <<EMPTY_NAME>> = 5.3;
Console.Write(5.4);
string b = Console.ReadLine();
bool flag = <<EMPTY_NAME>> == b;
if (flag)
{
Console.Write(5.5 + global::0.2 + 5.6);
}
else
{
Console.WriteLine(5.7);
global::0.2();
}
}
// Token: 0x04000001 RID: 1
public static string 0;
// Token: 0x04000002 RID: 2
public static string 1;
// Token: 0x04000003 RID: 3
public static string 2 = 5.8;
}
Debugging #
Now using the breakpoints in dnSpy I put one breakpoint in method 0.0 here:
if (flag2)
and another one in method 0.2 here:
if (flag)
Now let’s run the program and see what happens.
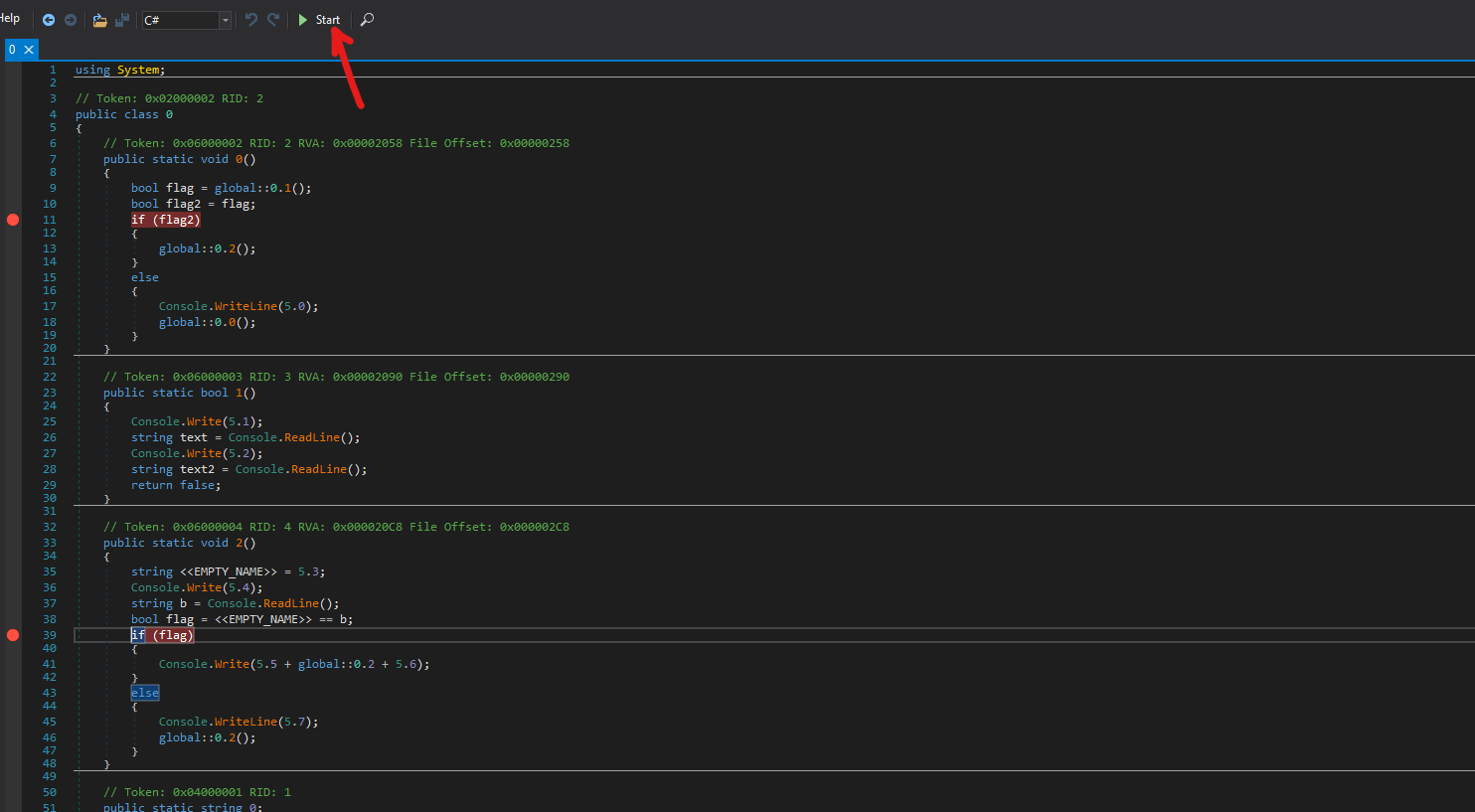 We can see that the program asks us for a username and a password, we can use random strings for both of them, I’ve used
We can see that the program asks us for a username and a password, we can use random strings for both of them, I’ve used test and test. The program stops at the first breakpoint, in the bottom of the picture we can see the value of the two variables flag and flags which are both false. We need to edit the flags to true so that the program will continue to the second breakpoint. Clicking on F10 dnSpy will step over the next instruction.
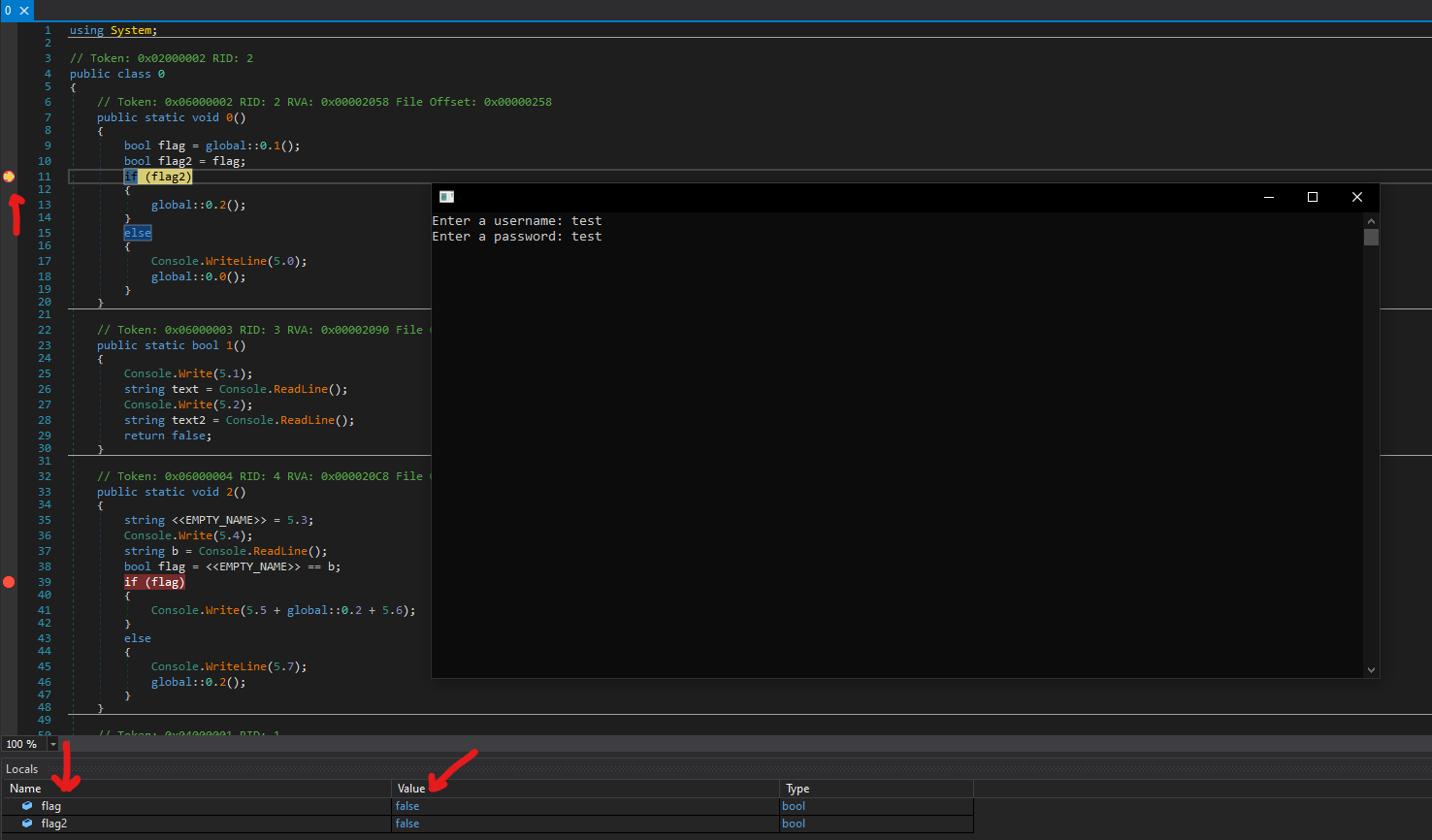
The program asked us to input the secret key, we can use again a random string, I’ve used 1234. After entering secret key the program stops at the second breakpoint, in the bottom of the picture we can see the value of the variable flag which is false and b is equal to 1234 that is the string we entered. We need to edit the flag to true so that the program will continue to the next instruction. Clicking on F10 dnSpy will step over the next instruction.
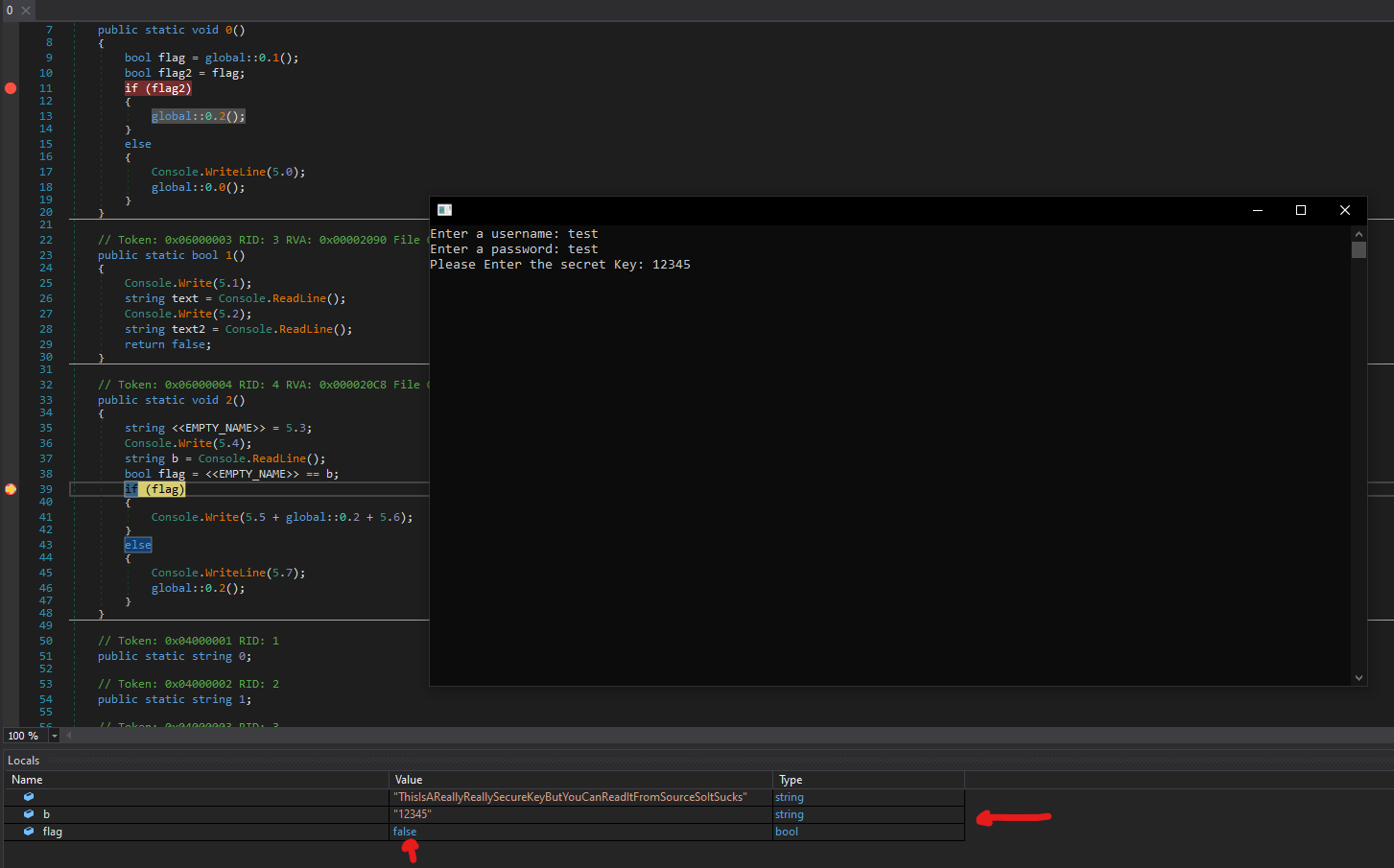
Now we arrived at the end of the execution of the program, we can see the flag in the console.
Enter a username: test
Enter a password: test
Please Enter the secret Key: 12345
Nice here is the Flag:HTB{.......................}
